IA GL20 Compliance Guide: Navigating Cybersecurity for Hong Kong Insurers
TL;DR: What Boards and Senior Executives Need to Know
- IA GL20 requires insurers to demonstrate cyber resilience, not just technical controls.
- Compliance is assessed through the Cyber Resilience Assessment Framework (CRAF): IRA, MA, and TIBAS.
- Most regulatory issues arise from governance gaps, weak risk articulation, and fragmented execution.
- With clear ownership and leadership oversight, GL20 can materially reduce regulatory, operational, and reputational risk.
Relevant for: Board members, Risk Committees, CROs, CISOs, Heads of IT, and Compliance leaders accountable for IA engagement.
GL20 reflects the Insurance Authority’s expectation that cyber risk is governed as an enterprise risk, comparable to financial or operational risk. Boards are expected to understand, challenge, and sponsor remediation outcomes—not merely approve submissions.
Understanding IA GL20 and CRAF
The Insurance Authority’s Guideline on Cybersecurity (GL20), revised in December 2024 and effective from January 1, 2025, formalises how insurers must assess and demonstrate cyber resilience. The focus is on protecting policyholder data (including PDPO-regulated personal data) and ensuring operational continuity during cyber incidents.
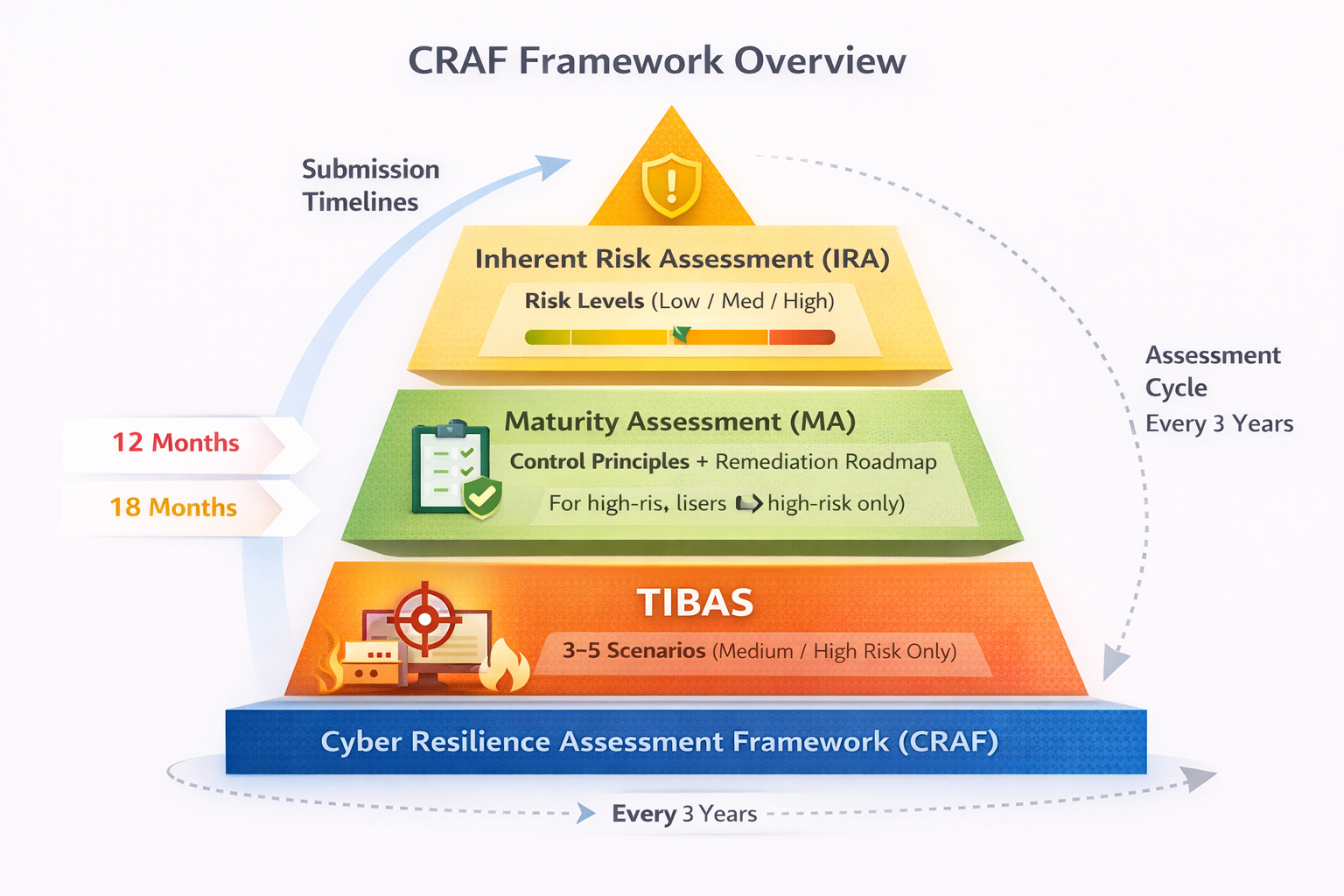
CRAF structures this expectation into three interdependent assessments. While many insurers already operate ISO 27001 or NIST-aligned programmes, GL20 raises expectations around evidence, integration, and outcomes.
1. Inherent Risk Assessment (IRA)
IRA establishes the insurer’s baseline cyber risk profile using 40+ indicators covering technology complexity, digital channels, outsourcing, and threat exposure. This risk rating directly drives assessment depth, supervisory expectations, and TIBAS applicability.
2. Maturity Assessment (MA)
MA evaluates whether governance, controls, and response capabilities are proportionate to the inherent risk. A remediation roadmap—with owners, priorities, and timelines—is a regulatory expectation, not an optional deliverable.
3. Threat Intelligence-Based Attack Simulation (TIBAS)
TIBAS is mandatory for medium- and high-risk insurers. It is an intelligence-led red team exercise conducted in production environments to test whether people, processes, and technology can withstand realistic attack scenarios targeting critical business functions.
Why GL20 Compliance Breaks Down
Based on market observations and regional project experience, GL20 issues rarely stem from lack of security tooling. They more often arise from governance and integration weaknesses.
Inadequate TIBAS Scope
TIBAS exercises that are limited in scenario breadth or disconnected from business risk fail to demonstrate resilience. Approximately 45% of insurers struggle to evidence meaningful scenario diversity.
Weak Maturity Gap Articulation
Where MA identifies gaps but lacks a credible remediation roadmap, regulators view this as ineffective risk management. Around 30% of submissions fall short in this area.
Underestimated Inherent Risk
Digital channels, mobile platforms, and outsourced services are frequently underweighted in IRA, leading to misaligned risk ratings and downstream assessment issues.
Third-Party Blind Spots
Third-party systems remain a dominant source of incidents. An estimated 35% of material breaches involve vendor environments that were insufficiently assessed or governed.
Limited Executive Engagement
When senior management involvement is superficial, remediation stalls and IA follow-ups increase. Regulators increasingly expect evidence of informed challenge and oversight.

A Board-Usable GL20 Execution Roadmap
Board / Risk Committee: Set risk appetite, sponsor remediation funding, challenge assumptions.
Management (CISO / IT / Compliance): Execute assessments, integrate findings, maintain evidence.
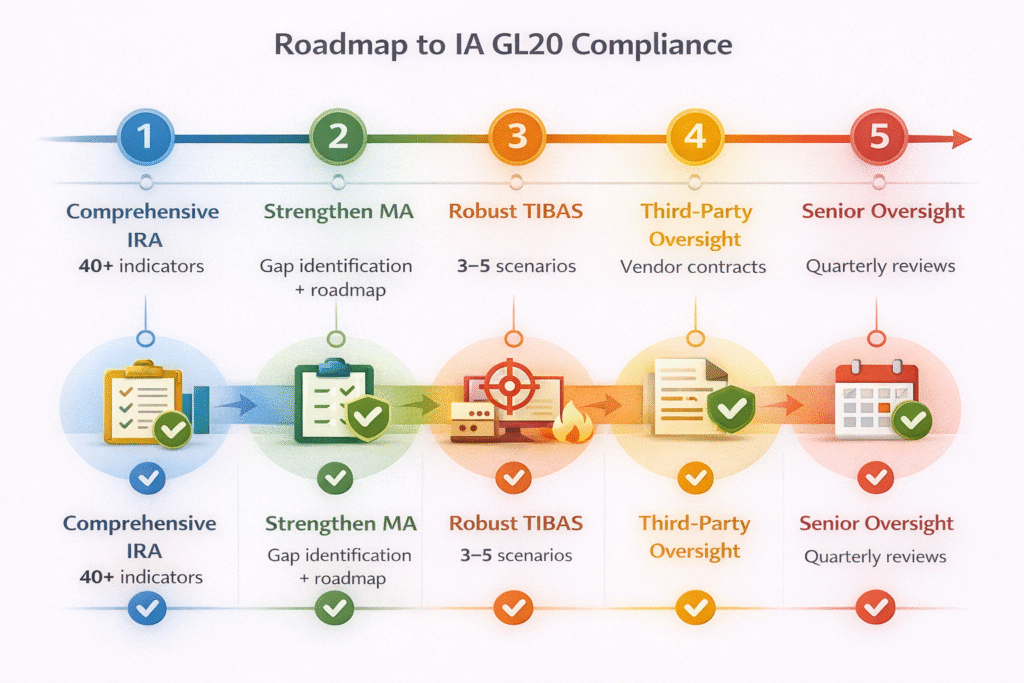
1. Establish a Defensible IRA
Ensure all 40+ indicators are addressed and documented. Medium- and high-risk insurers should consider IA-experienced external assessors to benchmark against peer practices and reduce regulatory rework.
2. Strengthen MA and Remediation Governance
Translate control gaps into funded, time-bound remediation actions integrated with enterprise risk and audit plans.
3. Execute Risk-Aligned TIBAS
Design 3–5 scenarios that directly map to IRA and MA findings, demonstrating a coherent, risk-based testing strategy.
4. Enforce Third-Party Accountability
Align vendor contracts, oversight, and escalation processes with CRAF expectations, particularly for critical service providers.
5. Maintain Ongoing Executive Oversight
Conduct periodic Board or senior management reviews to track remediation progress and emerging cyber risk trends.
Case Study: Leadership as the Turning Point
A 2025 breach affecting over 50,000 policyholders exposed weaknesses in mobile application risk assessment and a narrowly scoped TIBAS exercise.
The decisive factor in recovery was active Board and senior management sponsorship of the remediation roadmap, enabling faster decisions, funding approval, and cross-functional alignment. The insurer reduced critical vulnerabilities by 80% within six months and subsequently passed IA review.
How DarkCode Security Supports GL20
DarkCode Security helps insurers translate GL20 from regulatory text into defensible, IA-ready outcomes. Our support spans IRA and MA facilitation, intelligence-led TIBAS execution, and regulator-ready documentation aligned to IA templates.
If your IRA, MA, or TIBAS submission is approaching, we can help you reduce uncertainty, close gaps efficiently, and present a coherent risk narrative to the IA.
Contact us or visit darkcodesec.com/services.
- Tags:
- Compliance
- GL20
- Insurance